This is an old revision of the document!
Table of Contents
Higher end chips such as found in military devices and even commercial crypto devices can contain anti-tamper devices to protect designs and keys even if someone has gone this far. This page is for protections that physically render the chip inoperable, not obscurification techniques. Most common is to put a wire mesh over the chip. The idea being that if someone were to open up the IC, the mesh would get disturbed and turns the chip off. However, it is usually somewhat trivial to defeat this simply by connecting the entry and exit point of the mesh and bypassing the entire mesh network.
Live analysis wiring protection
A number of chips contain a key. If the key can be sniffed from the live running chip, the cards are compromised. A common way to prevent live analysis is to put a wire interlock mesh over the top of the top metal layer to ensure any breakages in the mesh causes the chip to be non-functional. However, these can usually be re-connected using probes. Example wire mesh:
Another technique, as used in the IBM 4758 crypto accelerator (http://www.cl.cam.ac.uk/%7Ernc1/descrack/ibm4758.html) is to pot the entire system inside a rubberized material which has had conductive paths doped through it. Any attempt at removing the material will disturb the wires and cause the card to zeroize itself. (This technique is especially powerful with units like the 4758 which are expected to be under power 24/7, with battery backup as needed: keys may be stored in RAM so the wires cannot be cut even with power removed.)
Static analysis wiring protection
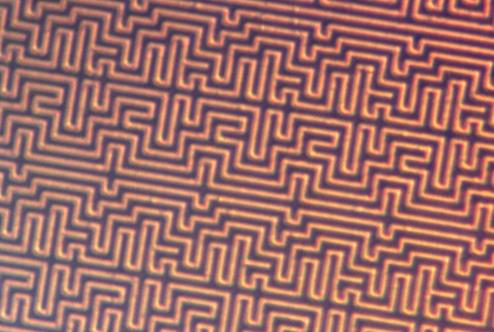
Obscurification techniques to make analyzing die images difficult. Most common is to make wires into a maze such that a human would get confused tracing them. However, computer aided techniques are largely immune to this.
Chemical protection
Very rare. I've been told that some high end military chips may have a thin layer of alkali metal put into them. The idea being if exposed to most techniques, it will react violently and destroy the chip. With proper chemical treatment and machining, such high end chip protections can usually be avoided. It may be best to destroy one chip to analyze protections and then attacking the actual chip to be imaged/tested.
UV metal shielding
Depending on technologies, circuits react differently to UV light. Metal shielding may be placed over circuitry to try to reduce the effectiveness of resetting/setting security fuses by UV light.
Die ID
National claims they have some sort of anti-reverse engineering protection with their die ID scheme. Who knows if it does anything useful.
Operator deterrents
We've read that some mil chips can have alkali metals to react with the strong acids typically used during decapsulation. This can be dangerous to the tech as well as destroy the specimen with the strong heat.
NanoFoil maybe? http://buy.solder.com/NanoFoil/C1019_1/
Patents
US5468990: Structures for Preventing Reverse Engineering of Integrated Circuits
References
- Hacking the PIC 18F1320: http://www.bunniestudios.com/blog/?page_id ======40